SNOWLEOPARD® Anti-Counterfeiting Technology, Overt-Covert Authentication
Plastics Product Security and Brand Protection Technology Solutions
Anti-Counterfeiting Solutions
Counterfeiting threatens the world economy and public health through the production of inferior products that circumvent consumer protection regulatory channels. Among the biggest challenges in fighting counterfeit goods is the need to stay ahead of counterfeiters using new and more sophisticated technologies.
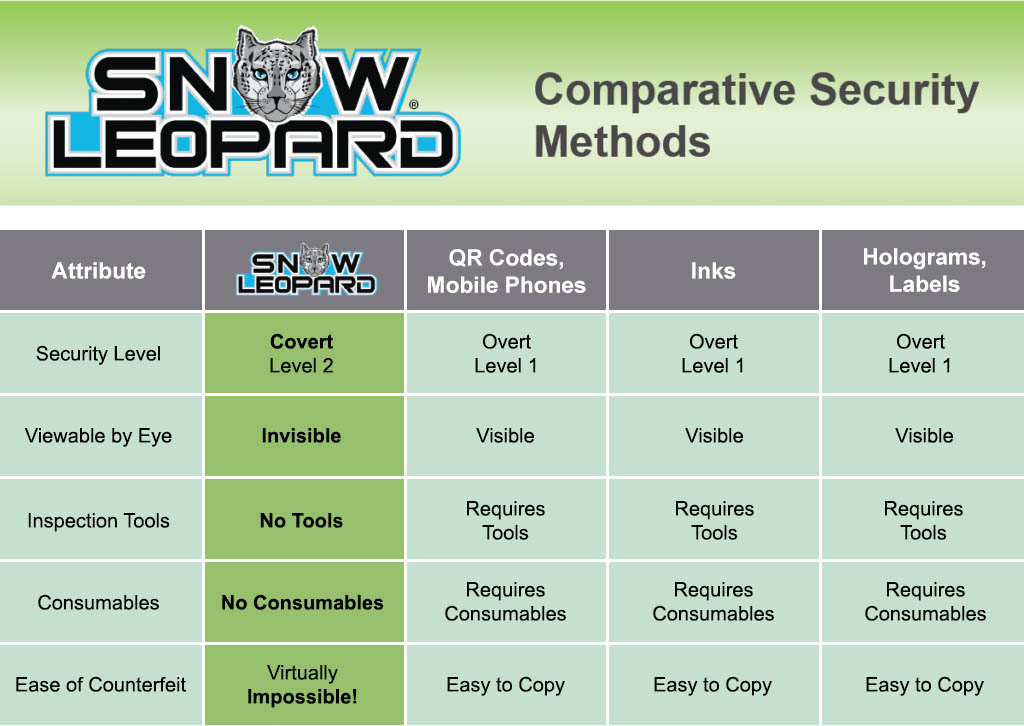
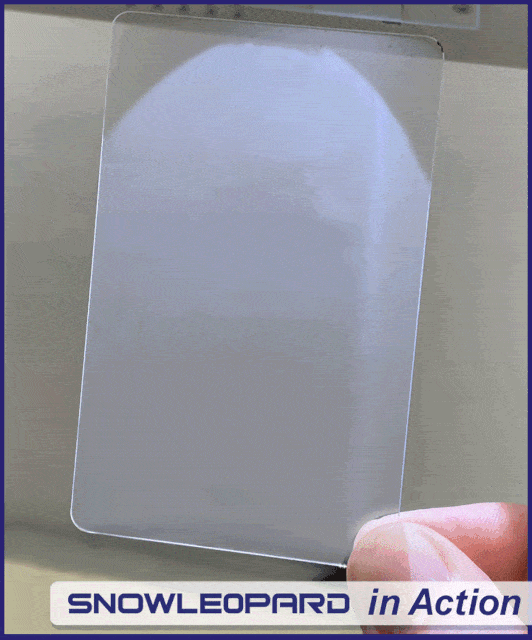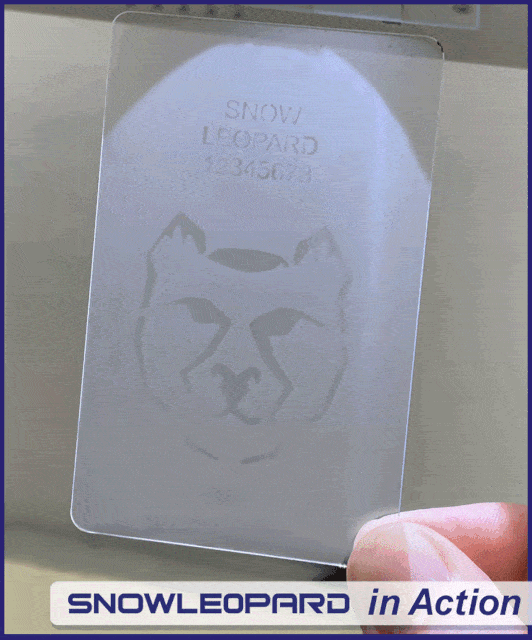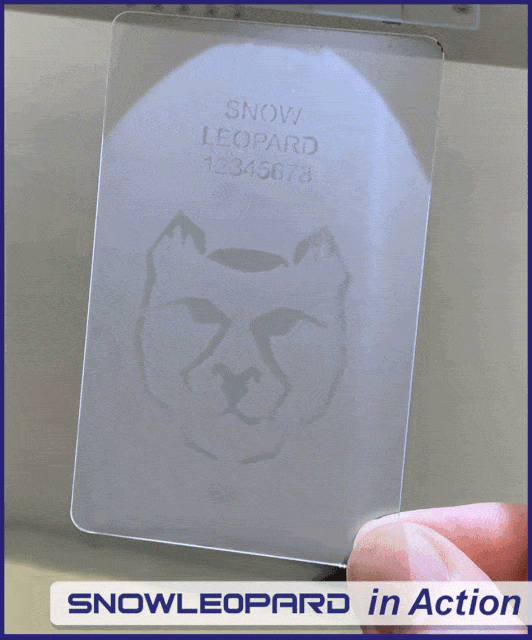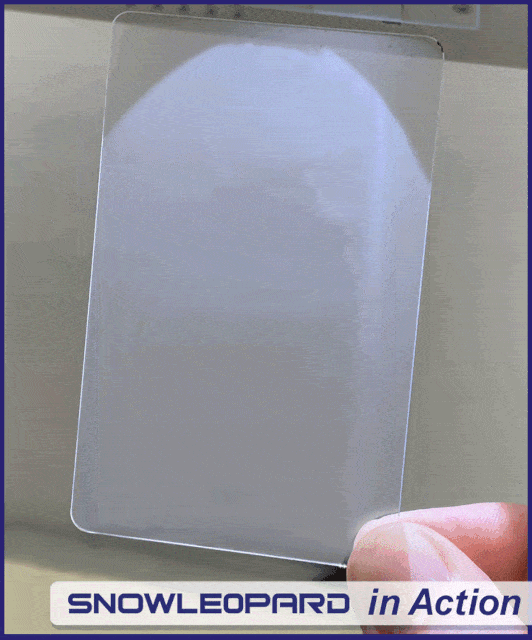
The Sabreen Group’s SNOWLEOPARD® anti-counterfeiting authentication solution is the newest generation of space-age engineering proven to stop counterfeiters. SNOWLEOPARD® utilizes invisible codes that are indelibly inscribed submicron on the product or packaging. Authentication by warm vapor mist is quick for the consumer – a single breath of air reveals hidden images, no smartphone cameras or special instruments. This simple phenomenon makes it easy for consumers to avoid being tricked by fake products. The application does not use any consumables, inks, printers, lasers, labels or holograms. Compare SNOWLEOPARD® with other anti-counterfeiting solutions.


Anti-Counterfeiting Technologies
Security features can be divided into three levels, i.e., Level 1 Security (L1S) (Overt), Level 2 Security (L2S) (Covert) and Level 3 Security (L3S) Forensic. These three levels of security in combination provide comprehensive layered security protection solutions. Overt and covert security authentication features are effectively incorporated into layered protection. Overt techniques are clearly visible and do not require detection devices. Covert technologies typically require specific equipment to be verified, as the details of the technology are not disclosed. Most of the recent developments in overt and covert technologies have embedded hidden features to make them more difficult to replicate illegally. Click here to view Anti-counterfeiting Technologies.
SNOWLEOPARD® vs. Other Anticounterfeiting Solutions
How Secure Are Common Anti-counterfeiting Solutions?
Traditional “physical” security features include hologram stickers, color shifting inks, chemical taggants, security graphics, micro marking & printing. Newer e-commerce digital solutions include QR codes, RFID and NFC chips which are connected to cloud-based platforms. While no single anti-counterfeiting technology can protect all products and circumstances there are important security and safety considerations. Experts and law enforcement assess the security risks of holograms and QR codes.
Optical variable devices (OVDs) including the category of holograms are overt images that exhibit various optical effects depending on the amount of light striking the OVD and the angle in which the OVD is viewed. In a 2019 publication by Securing Industry, the author states “there is an increasing trend among brand owners, and even some governments, to walk away from holograms as a security product. Holograms themselves became highly susceptible to counterfeiting and therefore trust in their effectiveness rapidly declined.” Key reasons cited include: the ease of duplication, cost to educate the public to properly verify and scrutinize specific optical effects, and a hologram is a passive entity not a true authentication process. Cheap replicas of expensive holograms are readily produced by criminals. The vast majority of consumers cannot distinguish between an original and an unauthorized fake. Criminals merely need to produce passable look-alikes.
QR (Quick Response) codes are square barcodes that a smartphone can scan and read to provide quick access to a website, download apps, and direct payments to intended recipients. Universal access offer bad actors easy methods of copying for purposes of fraud. Cybercriminals use several types of QR code exploits, phishing to steal credentials and QRLjacking to install malware. Hackers make their own QR code and delicately place it on top of legitimate codes, with most users unable to spot any maleficence. In January 2022, the FBI and cybersecurity experts warn about QR code privacy and security concerns. Privacy is also a concern and many consumers do not want third-party tracking of their personal data.